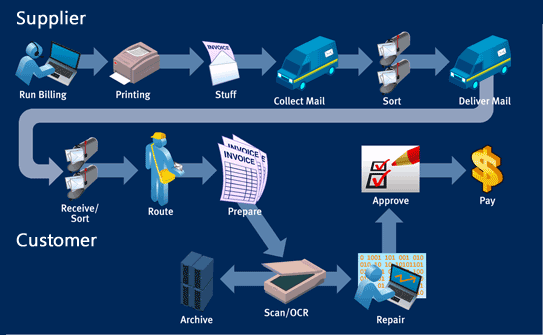
What do you need to look for when migrating to electronic invoicing software? Compliance? Ease of usage? Scalability? Of course, all of these, and much more. Since your financial processes involve clients, suppliers, and employees, you need bank-level security to keep things transparent yet secured. It is really hard to imagine business success if your sensitive data keeps falling in the wrong hands. So, security should be one of your primary requirements when looking for e-invoicing applications. Let us take a quick look at the best e-invoicing security features that you will need in your application.
A Thick Giant Firewall
Digital security should be your top priority, as you are conducting business online. Keeping your invoice data and e-mail contents away from the prying eyes can be possible with a strong firewall. It can create a barrier between the trusted and the dubious networks. You can create a list including the networks that you know are safe and bar everything else from accessing company or client data. You can also use the firewall to restrict information from getting out of your secured database, even through manual access.
Turn Your Data into Ciphered Text
Your e-invoicing software must have data encryption facility, as it is one of the most efficient ways to secure data. This is a process where your data is translated into a secret code, usable to only those who have the secret key. With an updated encryption facility, your invoicing process will achieve security in all regards.
Get Advantage of Mirroring Effect
Protecting data in just your computers is not enough when you are migrating to e-invoicing. You need to have failsafe security for your servers where the data is stored. E-invoicing software with server mirroring facility can contribute in resolving this issue. Backing up important data from the primary server and keeping it in a backup server can create a failsafe business consistency for you. With this facility you and your clients, suppliers, or employees, can always access or transact data even if the primary server fails. Redundancy in server computing is a necessity as your business grows roots in the online world.
Invoicing Must Go Through Validation
Your e-invoicing software must filter the invoice information through a data validation process. This process will check each invoice to extract information that your business structure needs to run through accounts payable. You can set the validation rules to reject incomplete or fake invoices. This way you can be sure that only authentic invoices are coming through. Needless to say, besides making your transactions secure, this feature will save time and resources by omitting manual intervention to pin-point errors in invoices.
Use Digital Signature for Security
A digital signature can help you steer clear from fraud and theft while using e-invoicing solutions. It creates and establishes a record to verify each digital document before sending it off to the inner sanctum of your e-invoicing stages. Digital signature process can be divided into three types such as electronic signature, advanced electronic signature, and qualified digital signature. Each one is capable enough to verify authenticity of documents. The first two signature types depend on logic and use previously recorded link between documents to verify authenticity. However, the last one uses a special device to record physical signature pattern and compares it to the documents before sending it to you. Thus, keeping fake or incomplete invoices out.
Security is a must when using electronic invoicing software, and looking for a few specific features in them before purchasing can help you make a better choice. Research, go through the websites of software providers, or shoot them an email for detailed information about the product features before signing a deal.